Key Takeaways
- CoinMarketCap’s entrance finish was compromised, displaying unauthorized pockets verification pop-ups to customers.
- The breach exploited a backend API vulnerability linked to the platform’s doodles characteristic, prompting an ongoing investigation.
Share this text
CoinMarketCap’s entrance finish was compromised on June 20, with its webpage displaying unauthorized pop-up messages asking guests to confirm their crypto wallets. The malicious pop-up was first flagged by a number of crypto group members.
The platform’s workforce confirmed the incident and warned customers towards connecting their wallets whereas they examine and work to resolve the difficulty.
🚨 Safety Alert
We’re conscious {that a} malicious pop-up prompting customers to “Confirm Pockets” has appeared on our web site.
⚠️ Do NOT join your pockets.
Our workforce is actively investigating and dealing to resolve the difficulty.
— CoinMarketCap (@CoinMarketCap) June 20, 2025
Blockchain safety service supplier Coinspect Safety has uncovered that CoinMarketCap’s backend API is delivering manipulated JSON payloads designed to inject malicious JavaScript by means of its rotating “doodles” characteristic.
🚨 CoinMarketCap’s backend API serves manipulated JSON information that injects malicious JavaScript by means of the rotating “doodles” characteristic. Not all customers see it, because the doodle proven varies per go to. The injected pockets drainer at all times hundreds for those who go to /doodles/ pic.twitter.com/13o9aB7JlW
— Coinspect Safety (@coinspect) June 20, 2025
Sure, CoinMarketCap drainer loaded from a “doodle” JSON file. Lottie is a JSON-based animation file format that permits designers to simply ship animations on any platform. We’re investigating this injection vector and different websites and dApps should contemplate it. https://t.co/hac2PdFe48
— Coinspect Safety (@coinspect) June 20, 2025
Additionally as we speak, Crypto Briefing observed indicators of an analogous safety incident on one other standard crypto web site.
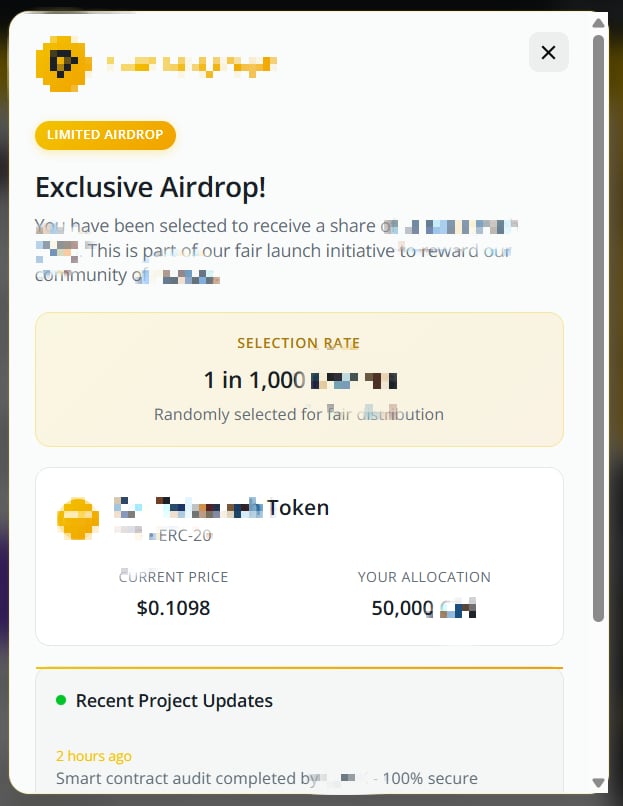

The webpage displayed a pop-up claiming an “unique airdrop” alternative, which was distinct from the CoinMarketCap incident however equally prompted guests to attach their wallets by means of claiming the airdrop.
Crypto Briefing was unable to verify whether or not the positioning’s front-end was compromised, on condition that the suspicious conduct appeared to final solely round 5 minutes. The positioning shortly returned to regular, and the pop-up was now not seen.
The breach follows a cybersecurity report from Cybernews revealing 16 billion uncovered passwords in one of many largest information breaches in historical past, affecting entry to main platforms together with Fb, Google, and Apple.
Specialists suggest that customers replace passwords for all main accounts, particularly these linked to delicate providers corresponding to work platforms. Customers are strongly suggested to make use of a password supervisor to generate robust, distinctive passwords for every account.
Further safety measures, together with enabling two-factor authentication (2FA) and carefully monitoring accounts, also needs to be thought-about.
Share this text















